By the time you finish reading this, your LLM could already be fixing vulnerabilities, querying your asset inventory, or triaging risks across your cloud footprint. Sounds like sci-fi? It’s not. It’s the JupiterOne MCP Server - a secure, standards-based foundation for AI automation for security teams.
When we think about the future of AI, we imagine systems that don’t just talk—they act. Not just respond—but reason, connect, retrieve, and remediate. You’ve worked in security and IT, you know the hardest part isn’t finding the data. It’s getting it in the right shape, at the right time, in the right place—so someone can actually act on it.
The tools don’t always talk to each other. The dashboards pile up. And you’ve got LLMs that can summarize incident response playbooks but still can’t tell you which EC2 instance has a vulnerable library exposed to the internet.
We built the JupiterOne MCP Server to help change that —by enabling agentic AI security that fits into your daily workflows.
What is MCP and why should you care
MCP—the Model Context Protocol—is the emerging standard for how large language models (LLMs) interact with the world: tools, data, and human intent. Think of it as the protocol layer that lets AI do things—securely, scalably, and contextually.
This server makes it possible for AI agents to access real security and IT data—and do something useful with it. It connects the dots between your assets, your vulnerabilities, your cloud posture, and the questions you’re already asking.
If you’re a security engineer, it helps you automate the checks you already do by hand.
If you’re a vulnerability analyst, it gives you real-time answers about exposure and ownership.
If you’re a Director of IT or Security, it helps your team reduce backlogs, surface risks earlier, and stay ahead of compliance pressure without writing new glue code every quarter.
This is about getting more value from what you already have—your data, your scanners, your asset inventory—and making that available to the models and agents you’re starting to trust.
What it does
The JupiterOne MCP Server works by exposing a set of tools and data that AI can use.
We’ve structured that into three parts.
Tools are actions the model can take—like running a query to find vulnerable assets, fetching ownership data, or kicking off a remediation task.
Resources are the data you want to bring into context. That could be a list of findings, a graph of asset relationships, or a time-bound report for a specific cloud account.
Prompts are reusable templates that help the model ask the right questions in the right format. They keep things consistent, fast, and clear.
Once the server is running, you can connect LLM to security tools like Claude, OpenAI Agents, or any other MCP-aware client. You give your model the ability to call tools and pull in relevant context—all with access control and security in place.
What this looks like day-to-day
Let’s say someone in your organization drops this into a Claude chat:
“Do we have any critical vulnerabilities on internet-facing assets running in production?”
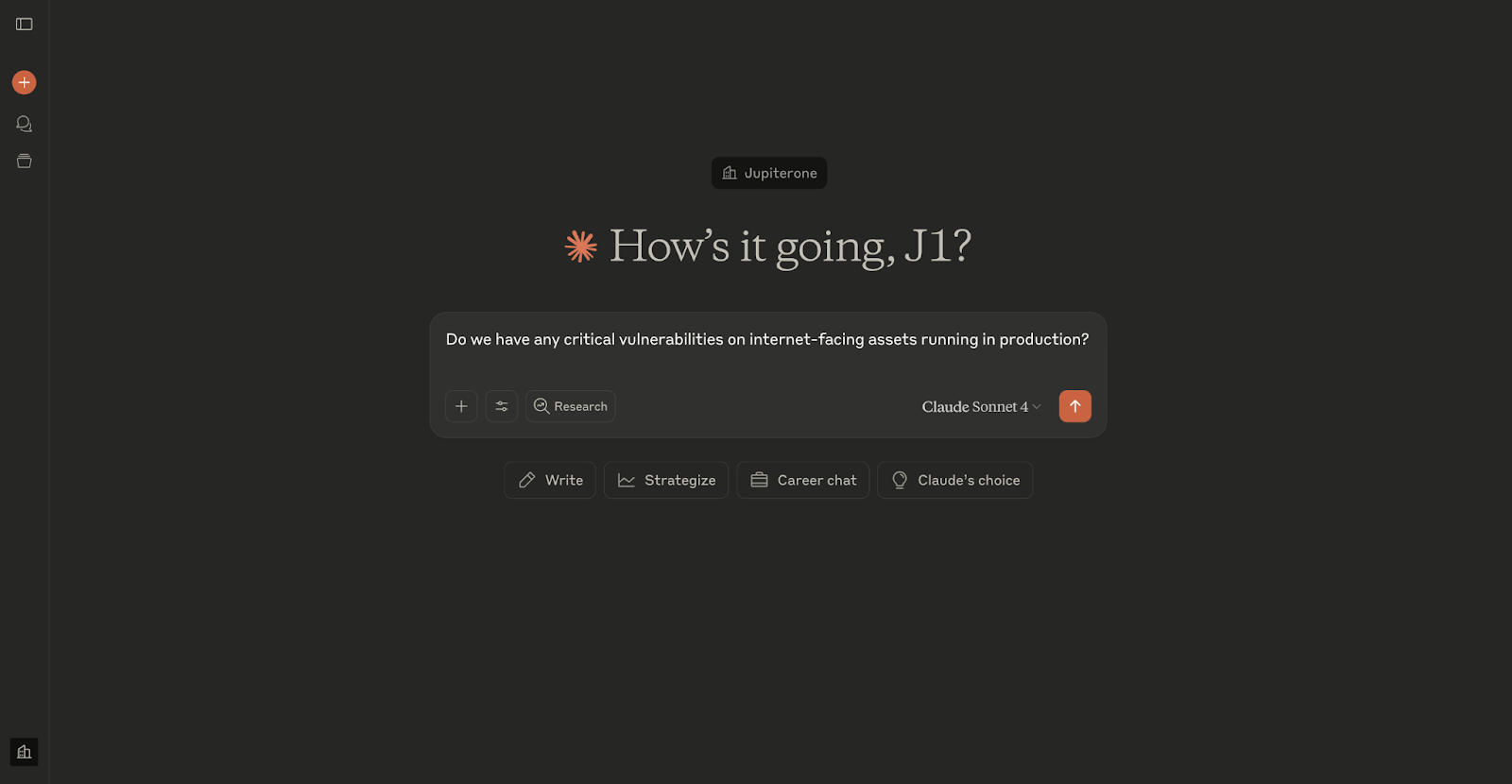
With the MCP Server plugged into your JupiterOne data, the model can go get the right answers. It can check the current asset inventory. It can match tags or labels to your “production” environment. It can pull vulnerability data that’s already been ingested. It can correlate that with exposure status.
And it can return a real answer—grounded in your live context—not just a guess. That’s the value of agentic AI security in practice.
You still decide what to do. But now, instead of digging through four systems and two exports, you have what you need in one place.
It works with what you already use
You don’t need to rebuild your stack.
The MCP Server runs alongside your existing setup. It connects to your JupiterOne environment, surfaces data through the protocol, and listens for requests from your LLM client. That’s it.
You can run it locally for testing. You can deploy it securely behind your firewall. It speaks HTTP, uses JSON-RPC, and follows the open MCP standard, so it fits right into your automation environment.
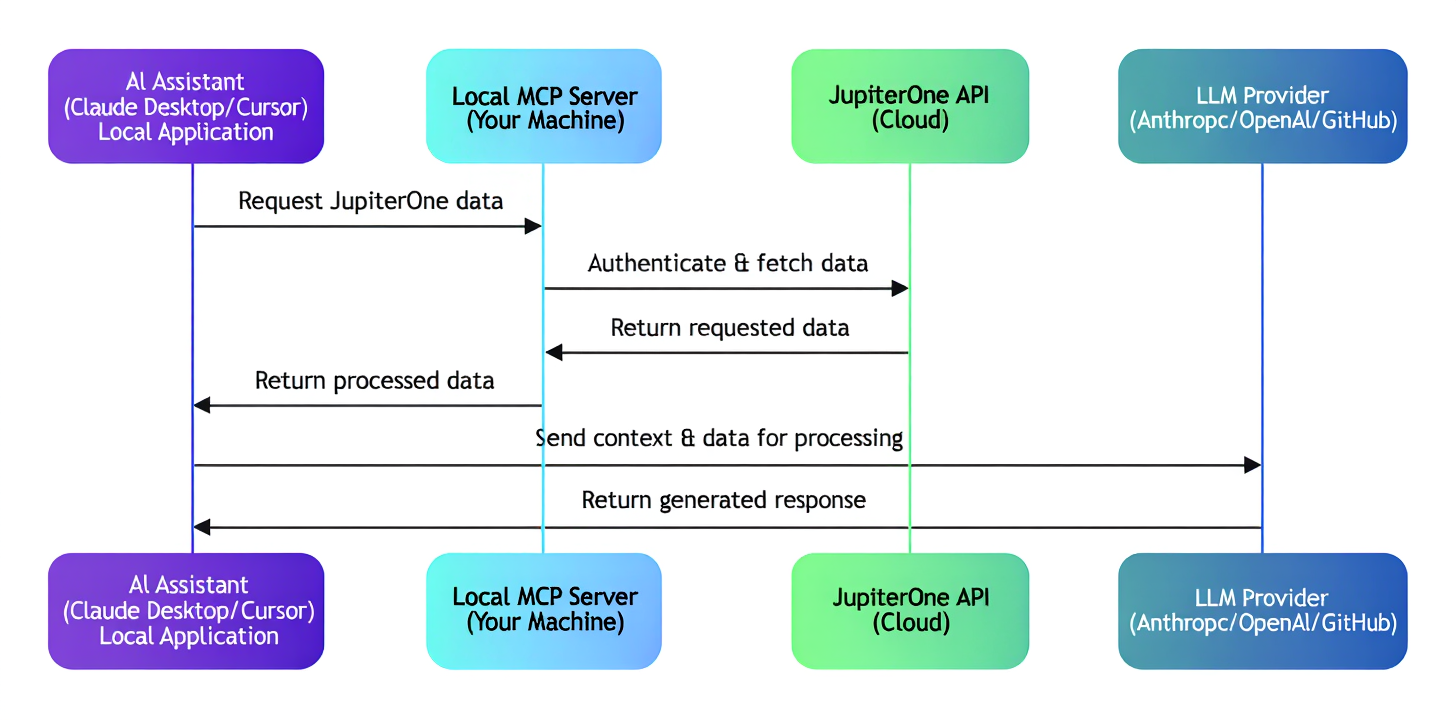
You can expose only the tools and resources you trust. You can change them at any time. You stay in control of what your AI can see and do.
Why now
Security teams are already underwater. Backlogs keep growing. Audit expectations are rising. And AI is showing up in every tool, every platform—but without a clear plan for how it actually helps security teams solve real problems.
This server is a small step toward fixing that. It’s a way to move from “this LLM looks promising” to “this LLM actually helped reduce our open findings this week.”
Gartner’s 2025 report on MCP said it best:
“MCP simplifies integration between AI models and enterprise data sources. It allows agentic applications to access tools and services in a structured, secure way—making them operational, not just conversational.”
This is about making agentic AI security part of your workflow—not a demo.
Getting started
We’ve made it simple to get going.
You can start by exposing one tool. One prompt. One resource. Watch how your AI assistant handles it. Then expand.
Add queries that matter. Hook into your vulnerability scanner. Let the model pull ownership info from your asset graph. Let it suggest triage. You stay in the loop. You approve the actions.
But now you’ve got a partner that understands your data—and can actually work with it.
If you're leading a security team and looking for ways to use AI responsibly, this gives you a safe, clear, and standards-based place to start.
If you're in the weeds doing the actual analysis and remediation, this is a way to spend less time digging and more time deciding.
And if you’ve ever wished your LLM could help you do security—not just talk about it—this is the beginning of that future.
The JupiterOne MCP Server is available now.
Let us know what you build with it.