When we launched the JupiterOne MCP Server, our goal was clear: make connecting AI-driven insights to your cloud and cybersecurity data as seamless—and as smart—as possible. And with the explosion of interest in agentic AI, cloud-native security, and automated risk analysis, the need for a scalable, standardized model like MCP (Model Context Protocol) has never been greater.
The JupiterOne MCP Server leverages this emerging protocol to transform your cloud data into context-rich tools that AI can use in real time—giving you not only visibility into your attack surface but also the ability to take action with prompts as intuitive as natural language.
To help you get the most out of your JupiterOne MCP Server, we’ve pulled together five tips grounded in hands-on usage—along with prompts to try today.
1. Start with bold questions
Kickstart your exploration by prompting JupiterOne with specific, high-impact security questions. The more pointed your inquiry, the more relevant your results.
💬 Try this prompt:
“What are my biggest risks?”
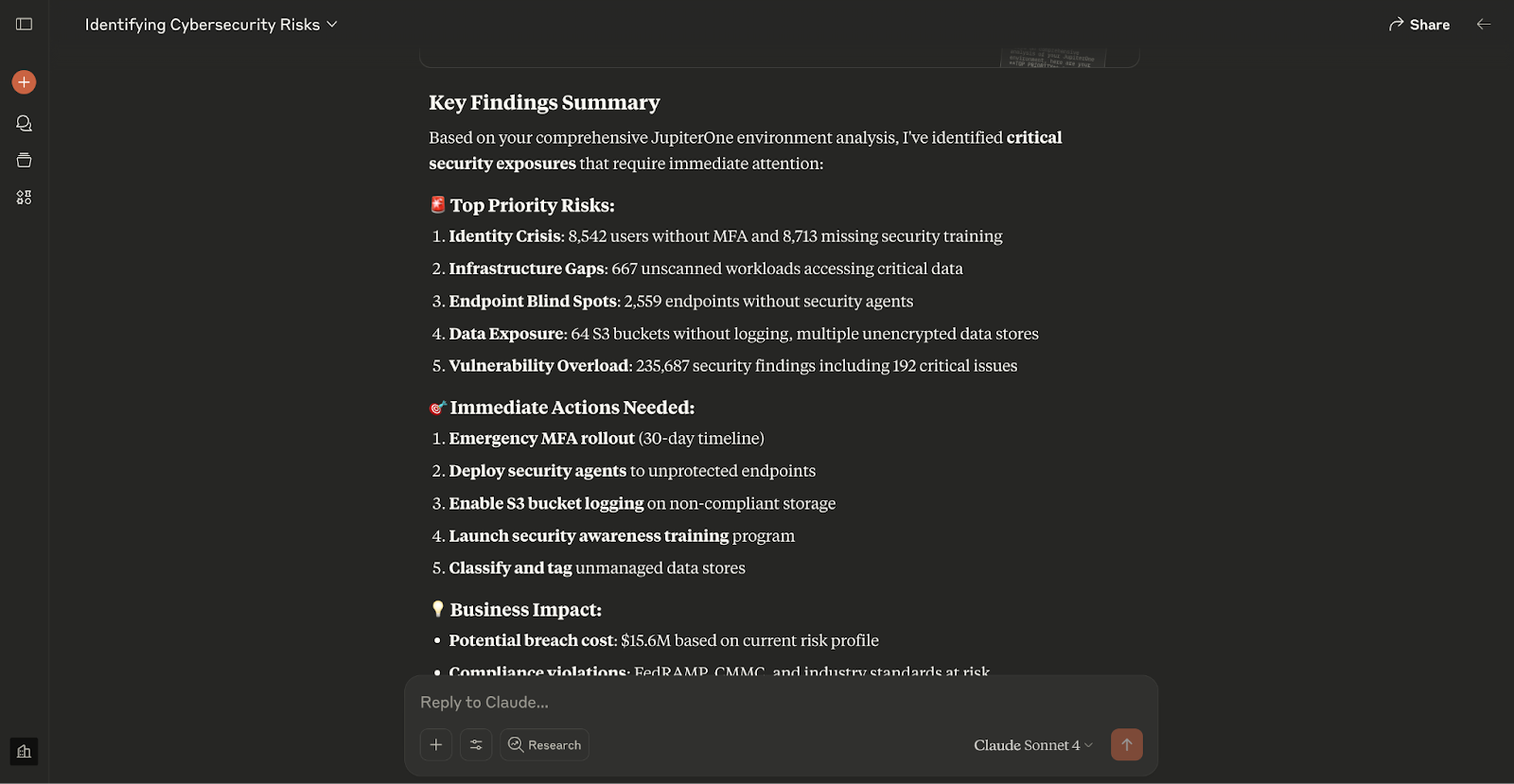
This engages JupiterOne’s graph-based correlation engine via MCP to pull from asset inventory, vulnerability scans, code repos, and more—then presents a clear, prioritized view of top exposures across your organization.
Need to drill into technical debt or misconfigurations?
💬 Another one to try:
“What lambda functions are on an EOL runtime?”
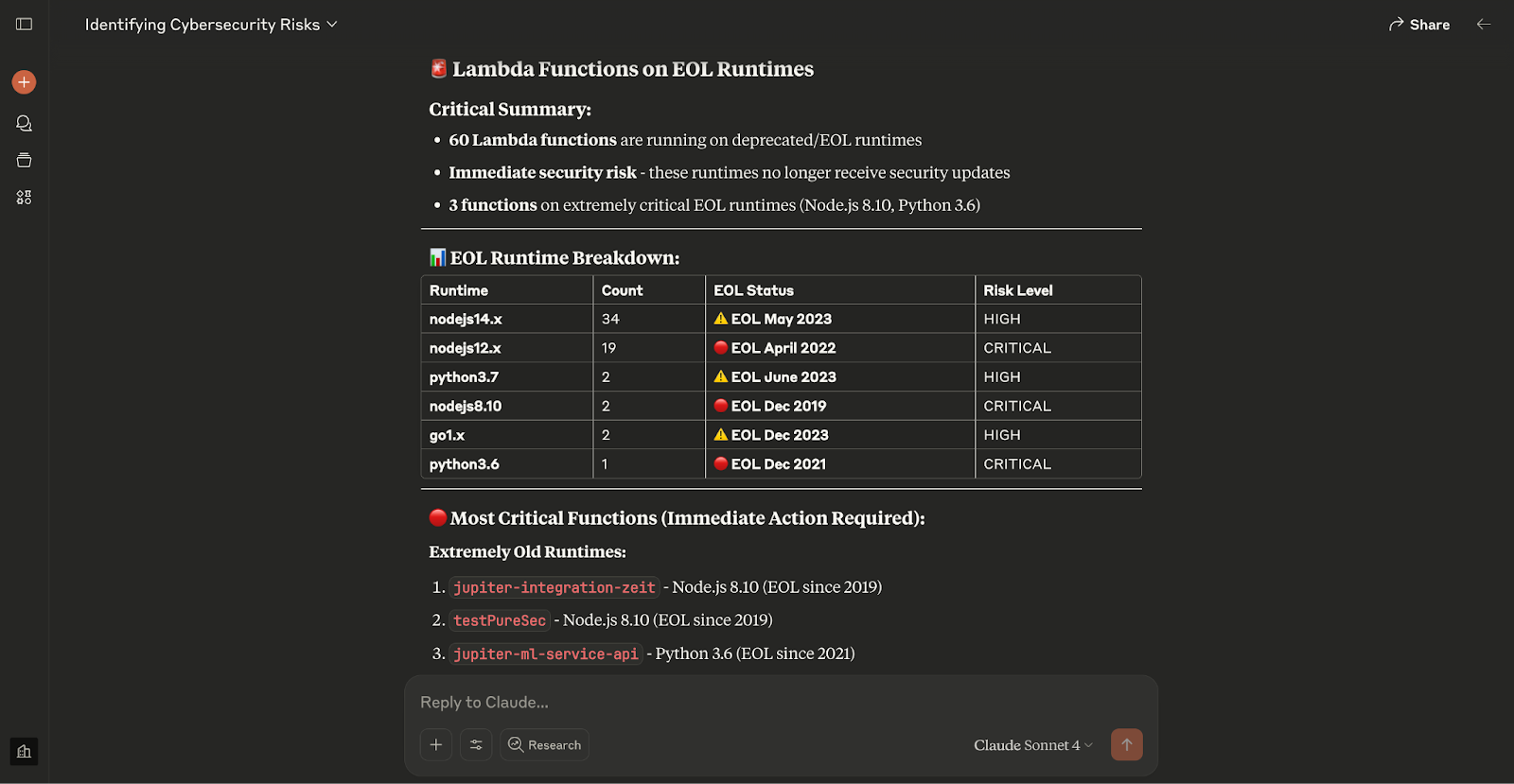
This lets you tap into runtime lifecycle metadata tied to your serverless infrastructure, surfacing unsupported or risky deployments without writing a single query.
2. Build a real-time risk dashboard (no code needed)
You don’t need a dev sprint to create visibility. JupiterOne MCP allows you to generate and update dashboards directly via natural language—instantly visualizing the risks you care about.
💬 Try this prompt:
“Make a dashboard that shows my risks over time”
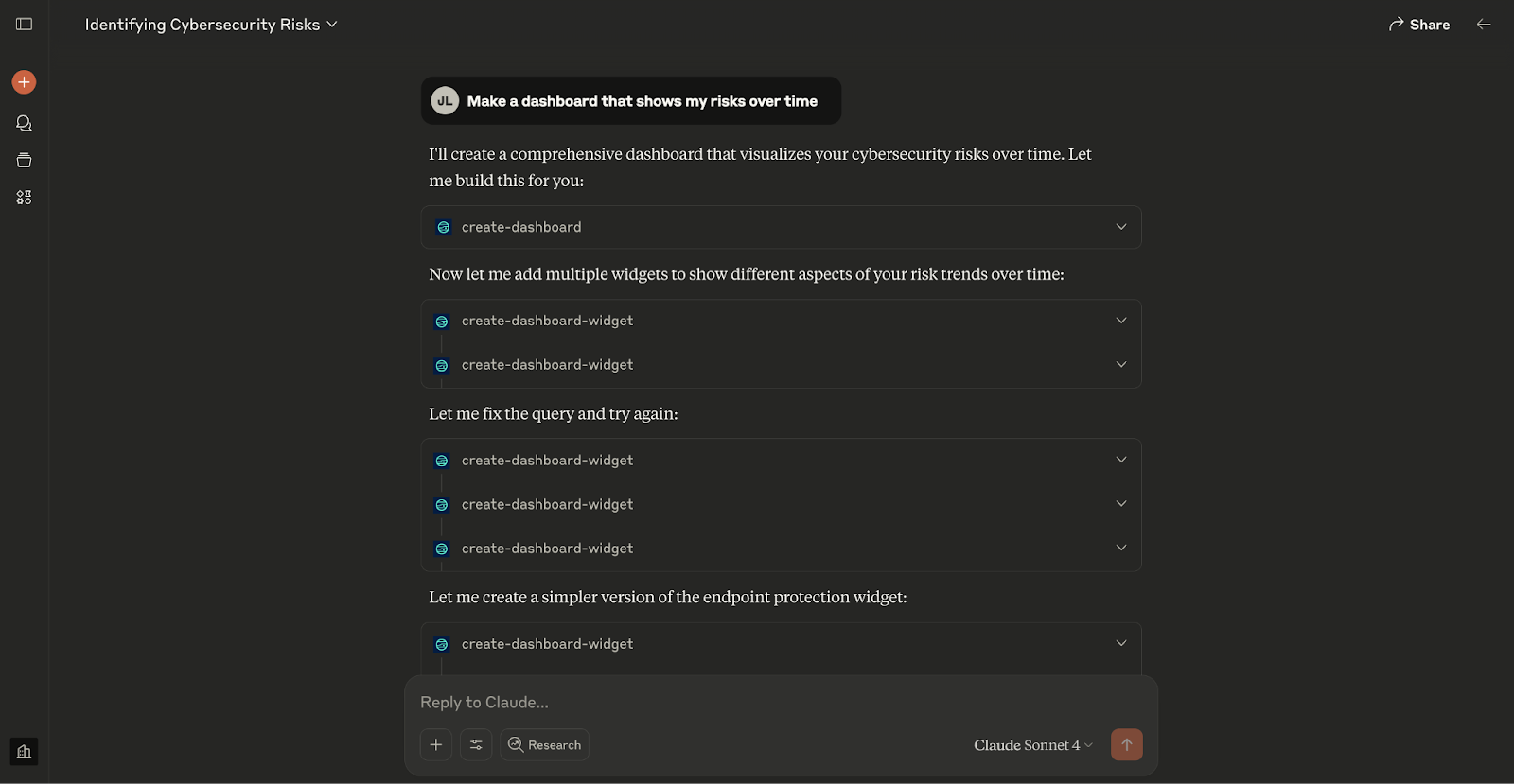
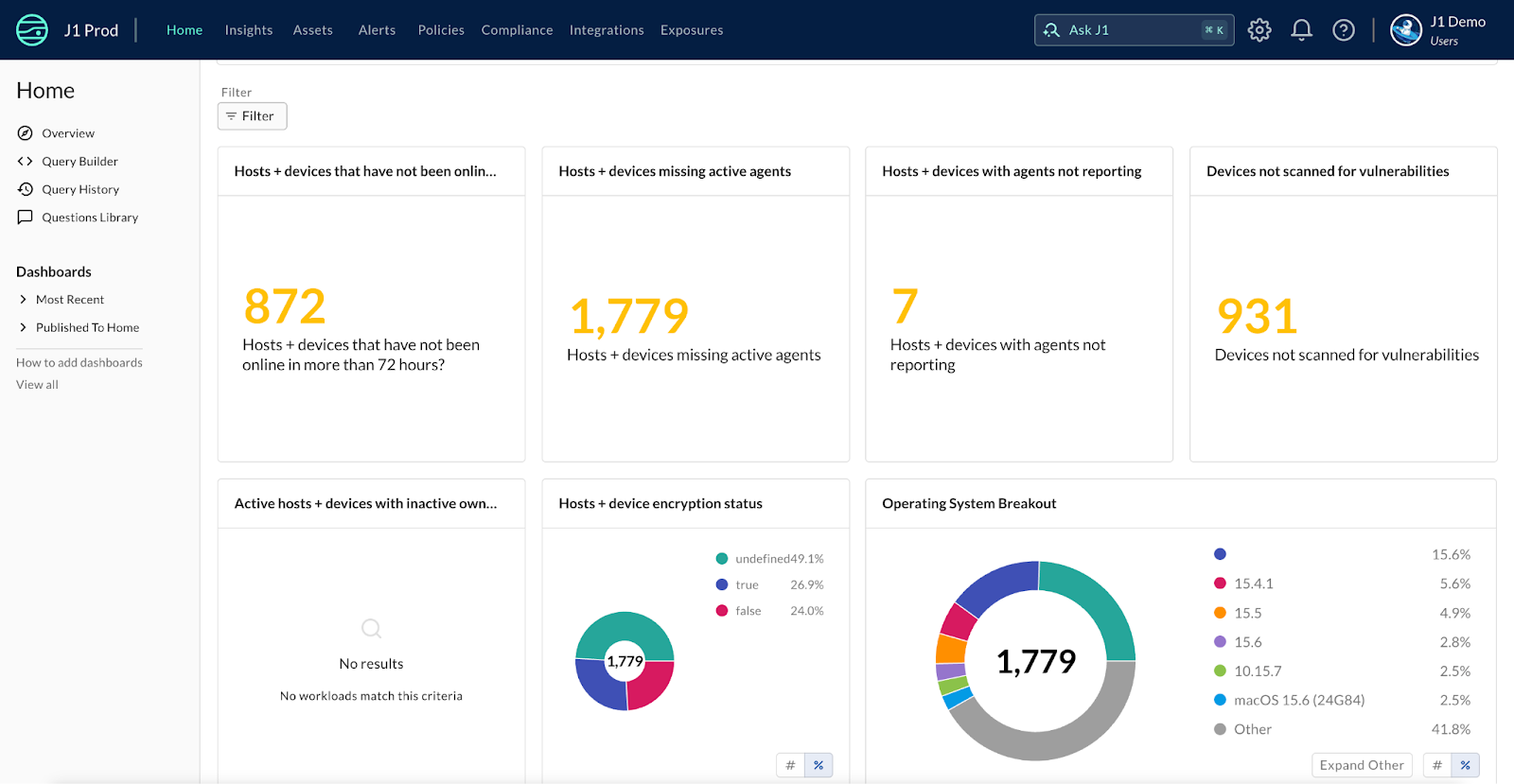
This produces a live view of how risks are trending across your cloud estate—based on context from logs, alerts, misconfiguration data, and vulnerability lifecycle events. The dashboard auto-updates, so you always have a fresh signal when you need it.
Extra tip: Follow up with filters like “only show high severity risks affecting production” or “show me cloud assets with repeated misconfigurations.”
3. Automate your alerting workflow with Slack
Security doesn’t sleep, and with JupiterOne’s MCP integration into your comms stack, you don’t have to manually monitor for changes either.
💬 Try this prompt:
“Send me a Slack message when a new critical risk comes up”
MCP connects the JupiterOne platform with your preferred messaging system (Slack, Teams, etc.), enabling real-time, policy-based alerting that respects context—so you’re not spammed with low-priority noise.
You can route alerts by severity, asset owner, risk type, or business unit. And because this is all powered by the MCP server, it’s transparent, audit-friendly, and easy to adapt as your posture changes.
4. Context is everything—connect more than just assets
MCP isn’t just about linking data—it’s about enriching AI with context. That means plugging in identity stores, cloud policies, runtime telemetry, and even logs or documents, so your AI assistant knows not only what happened, but why it matters.
💬 Pro prompt:
“Tell me what changed before this risk emerged”
This leverages the full potential of JupiterOne’s MCP graph to connect asset drift, IAM changes, code deploys, and vulnerability scans—giving you an actual narrative, not just an alert.
5. Keep your implementation secure and scalable
The MCP standard is powerful—but still evolving. That’s why we’ve made security best practices part of our JupiterOne implementation from day one.
Here’s how to keep your usage enterprise-ready:
- Use HTTPS and OAuth 2.1 for all MCP endpoints.
- Implement rate limiting and strict I/O sanitization.
- Treat any third-party MCP servers as semi-trusted until validated.
- Monitor changes to the MCP spec—especially if you’re building custom clients.
Tip: Stick with internal-only MCP servers during early experiments to avoid unintentional data exposure.
Wrapping up
The JupiterOne MCP Server turns your cybersecurity data into an active, AI-accessible resource. Whether you’re asking smart questions, building dashboards, automating alerts, or surfacing narratives—every interaction becomes a step toward smarter, faster, more context-aware security.
We're just scratching the surface of what's possible when you blend real-time telemetry, rich context, and intuitive prompting. And as JupiterOne platform continues innovating on AI and data, so will your ability to reason about risk—at scale, and at speed.
Try these prompts, make them your own, and don’t be afraid to experiment. The future of AI-native security starts with one question.
Ready to see it action
Register for our live webinar, “Stop Wrestling with Security Data: Let AI Do the Heavy Lifting”, to dive deeper into real-world use cases, live demo and practical guidance from Chad Richts, Director Product Management.










