Most security teams have solved the endpoint visibility problem. When someone spins up a VM without an EDR agent, you know about it in minutes. Real-time alerts fire. Tickets get created. Coverage gaps get closed before they become audit findings—or worse, breach vectors.
But ask the same teams about their container and Kubernetes environments and you'll hear a different story. Clusters spin up fast. Workloads are ephemeral. And the runtime security sensors that protect those environments? Whether they're deployed on every new workload is often verified the old-fashioned way: pulling reports from multiple consoles and manually reconciling them to find the gaps.
That's a visibility problem. And as cloud-native architectures become the default compute layer across the enterprise, it's an increasingly dangerous one.
Today, we're announcing the general availability of the JupiterOne integration with Upwind, a cloud-native application protection platform (CNAPP) recognized in Gartner's 2025 Market Guide for CNAPP. This integration brings Upwind's runtime cloud security data—including configuration findings, misconfigurations, and compliance posture—directly into JupiterOne's asset graph, giving security teams the same level of continuous coverage monitoring for cloud-native environments that they've long had for traditional endpoints.
The CNAPP Data Problem Nobody Talks About
The CNAPP market exists because cloud-native environments introduced security challenges that legacy tools were never designed to handle. Gartner estimates that the market segments converging into CNAPP—spanning cloud security posture management, cloud workload protection, application security testing, vulnerability assessment and web application and API protection—represented over $13 billion in combined spending at the end of 2024, with double-digit growth across every category.
Organizations are investing heavily in CNAPP platforms. But here's the problem: even the best CNAPP generates findings in isolation. It tells you a container is misconfigured. It flags a workload missing a runtime sensor. What it doesn't tell you is how that finding connects to everything else in your environment—the applications that depend on that workload, the data that flows through it, the identities that can access it, or the compliance frameworks it maps to.
That's where the graph comes in.
A Partnership Built Around the Complexity Customers Actually Face
Enterprise environments don't run on a single platform, and they can't be secured by one either. Attack surfaces now span multi-cloud infrastructure, containerized microservices, serverless functions, SaaS applications, on-premises systems, and the identities that connect them all. The challenge isn't a shortage of security tools—it's that each tool sees its own slice of the environment without understanding how the pieces fit together.
The JupiterOne and Upwind integration was built around this reality. Each platform solves a distinct and critical part of the problem, and the combination delivers something neither can alone.
Upwind provides deep, runtime-first cloud-native security. Where many CNAPP vendors began with static posture management and are working toward runtime capabilities, Upwind was purpose-built around what Gartner's 2025 Market Guide identifies as recommended, advanced-tier CNAPP capabilities: agent-based runtime visibility into VMs, containers, and serverless functions, real-time runtime analysis of live workloads, and API discovery and monitoring. The data Upwind produces isn't based on periodic scans or point-in-time snapshots—it reflects what's actually happening inside production environments right now.
JupiterOne provides the asset graph that connects security findings to organizational context. With over 200 integrations spanning cloud providers, identity systems, endpoint tools, code repositories, and now CNAPP platforms, JupiterOne normalizes and correlates data across the full attack surface. It maps relationships between assets, traces ownership and dependencies, and continuously monitors whether security controls are in place across the environment.
Together, runtime intelligence from Upwind meets asset context from JupiterOne. A CNAPP finding gains meaning when you can see that the affected workload is internet-facing, processes regulated data, has three downstream service dependencies, and falls under a compliance control that's due for evidence collection. That's the kind of context that turns alert volume into prioritized action.
The Problem in Practice
Here's a scenario that plays out daily in enterprises running hybrid and cloud-native workloads.
Your EDR platform is integrated with JupiterOne. You've built alert rules. The minute someone provisions a host without an endpoint agent, your team gets notified. Coverage stays tight, evidence flows into your compliance framework and your auditors are satisfied.
Now someone spins up a new cloud-native workload—a container cluster, a serverless function, a new microservice. JupiterOne sees it immediately through your cloud provider integration. But does that workload have runtime security coverage? JupiterOne knows the asset exists. What it couldn't tell you—until now—was whether a CNAPP sensor was protecting it.
Without this integration, closing that loop meant pulling data from multiple systems and manually comparing it. By the time the analysis was done, the environment had already changed. New workloads had spun up. The gap report was already stale.
What the Integration Delivers
The JupiterOne + Upwind integration eliminates that gap by bringing Upwind's CNAPP data into the same graph where your cloud infrastructure, identities, code repositories and endpoint telemetry already live.
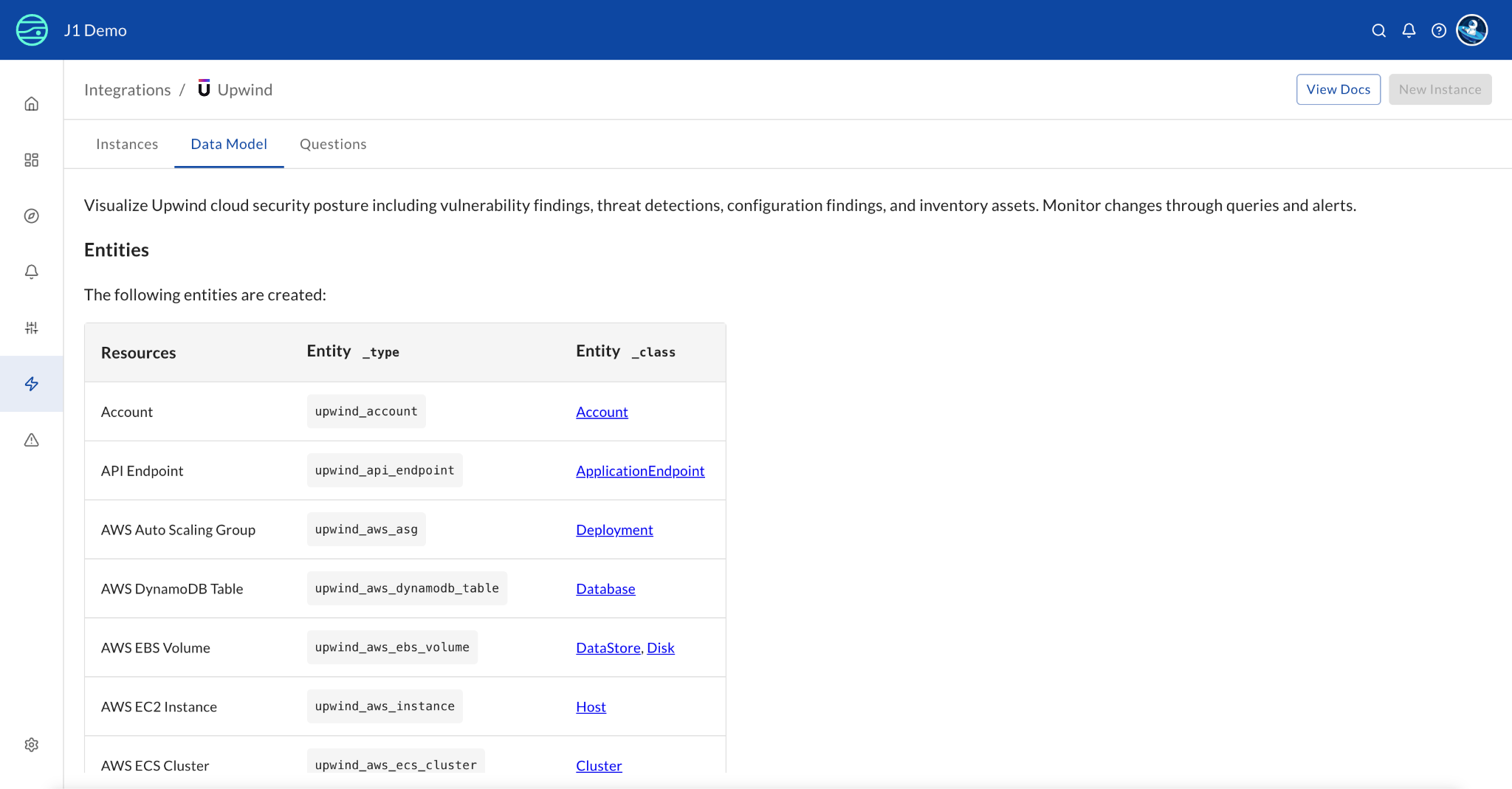
How it works: JupiterOne's managed integration authenticates to the Upwind API and periodically ingests configuration findings, misconfigurations, and compliance data. That data is normalized into JupiterOne's entity-relationship model, where Upwind findings become first-class graph entities with typed relationships to the cloud resources, accounts and workloads already in your environment.
Once connected, you unlock capabilities that neither platform delivers alone:
Detect coverage gaps in real time. Build J1QL queries and alert rules that fire whenever a cloud-native workload exists without a corresponding CNAPP sensor—exactly the way you already monitor EDR coverage on hosts. No more manual reconciliation across consoles.
Add asset context to runtime findings. Upwind tells you a workload has a misconfiguration with real-time, runtime-validated evidence. JupiterOne tells you that workload is connected to a public-facing application that processes regulated data and is owned by a specific team. That's the difference between a finding and a prioritized risk.
Automate compliance evidence. Upwind's configuration findings map directly to compliance frameworks within JupiterOne's Continuous Controls Monitoring (CCM). Whatever framework your organization operates under—whether it's CIS benchmarks, PCI-DSS, or any of the major regulatory and industry standards—Upwind becomes another automated evidence source, replacing the manual effort that makes audit cycles painful.
Trace blast radius through the graph. When Upwind surfaces a real-time detection or misconfigured resource, JupiterOne's graph traversal lets you trace the relationships outward: what services depend on it, what data flows through it, who owns it and what the downstream impact of exploitation would be. This is attack path analysis grounded in both runtime reality and organizational context.
Why This Matters
This partnership addresses three challenges that grow more urgent as enterprise attack surfaces expand:
Parity between endpoint and cloud-native security monitoring. Your board and your auditors expect the same rigor around Kubernetes and container security that you've established for endpoints. Agent-based runtime visibility—which Gartner positions as the recommended tier for cloud workload protection—needs the same continuous coverage monitoring you apply to EDR. This integration makes that achievable without building custom automation or accepting manual processes.
A unified view of a fragmented attack surface. The average enterprise runs 70+ security products. Each one sees its own slice. The JupiterOne and Upwind partnership connects runtime cloud-native findings to the broader asset graph—cloud infrastructure, identities, endpoints, code, and data—so security teams can reason about risk across the full environment rather than within the boundaries of any single tool.
Evidence-driven compliance at speed. If your compliance process still involves chasing evidence across tools before every audit cycle, this integration changes that. Continuous Controls Monitoring (CCM), powered by real-time data from Upwind's agent-based runtime analysis, replaces point-in-time evidence gathering with always-on assurance.
For the Practitioner: Getting Started
Setting up the integration is straightforward:
- Generate API credentials in your Upwind console.
- Configure the Upwind integration in JupiterOne with your API key and endpoint.
- JupiterOne begins ingesting Upwind configuration findings, misconfigurations, and compliance data on a configurable schedule.
- Use J1QL to query across Upwind data and your existing asset graph.
Here are a few starter queries to explore:
// Find cloud workloads without Upwind coverage
FIND aws_eks_cluster THAT !HAS upwind_finding
// Show Upwind misconfigurations on internet-facing resources
FIND upwind_finding WITH severity='HIGH'
THAT RELATES TO * THAT ALLOWS Internet
// Compliance evidence: list all Upwind findings mapped to CIS controls
FIND upwind_finding WITH complianceFramework='CIS'
Full integration documentation is available at docs.jupiterone.io/integrations/directory/upwind.
Better Together: CNAPP Needs the Graph. The Graph Needs Runtime.
Enterprise attack surfaces aren't slowing down. Cloud-native adoption is accelerating, workloads are becoming more ephemeral, and the number of assets, identities, and dependencies a security team must track grows every quarter. No single platform—no matter how capable—can solve that problem alone.
Upwind provides real-time runtime analysis producing high-fidelity, runtime-validated signals that enterprise security teams need.
JupiterOne's asset graph turns that signal into context. It connects Upwind's findings to the rest of the environment—cloud infrastructure, identities, endpoints, data stores, compliance frameworks—and gives security teams a single place to understand relationships, trace blast radius, monitor control coverage, and prioritize what matters most.
This partnership reflects a simple conviction shared by both teams: security leaders shouldn't have to choose between depth and breadth. They need both. Runtime depth from Upwind. Attack surface breadth from JupiterOne. And the integration layer that makes them more valuable together than apart.
Because the question isn't whether you can see your cloud-native assets. It's whether you can see what's protecting them—and what's at stake if they're not.
Ready to close the cloud-native coverage gap? Configure the Upwind integration in your JupiterOne account today or contact us to see a demo.









