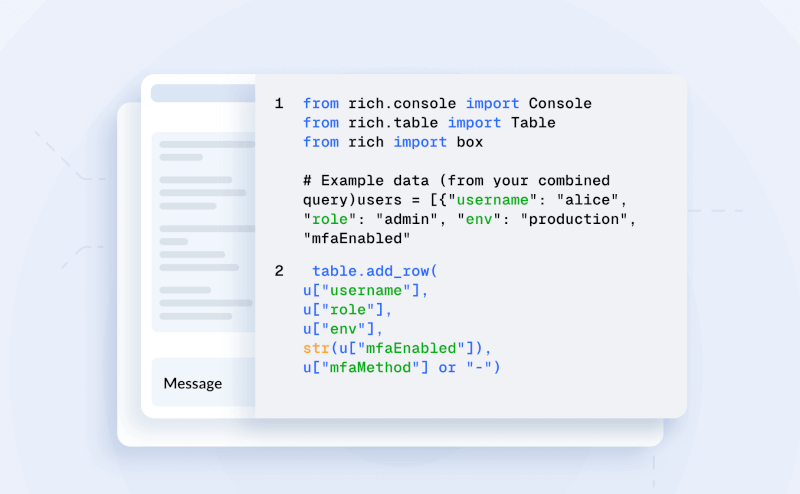
Test hundreds of security controls continuously at enterprise scale.
The only continuous controls monitoring solution built on a graph architecture. Prove your controls work in production, not just on paper.
Your compliance program can't answer: Are our controls working right now?
Testing Doesn't Scale
You're validating 20 controls manually while your security program requires 200. Your team can't keep pace with the infrastructure they're supposed to protect.
The IRM Gap
Your IRM platform says "MFA enabled on all privileged accounts." Your production environment says otherwise. The gap between what compliance documents claim and what's actually deployed is invisible until an audit or breach exposes it.
Quarterly Validation, Daily Changes
You're proving controls worked during last quarter's audit window, not that they're working right now. Every screenshot is stale the moment it's captured.
From scheduled checks to nonstop validation.
Define and verify your security controls in real time with JupiterOne CCM

Seize control over your data
Continuous Evidence Engine
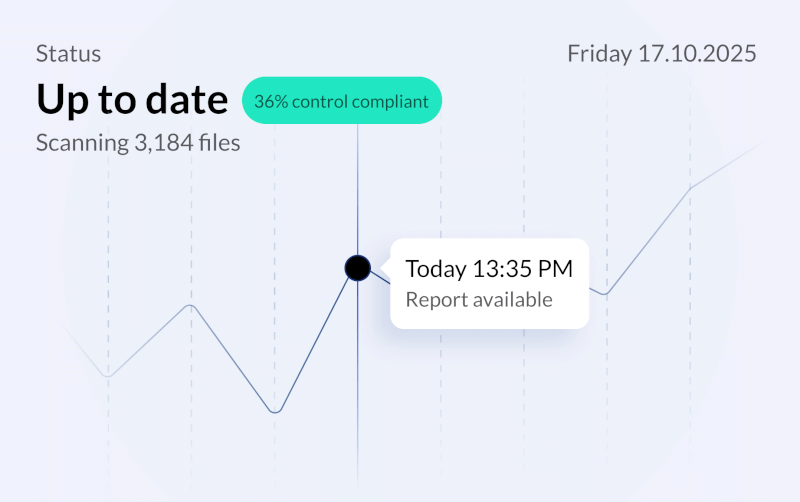
Every control test automatically generates tamper-proof evidence. Query your security posture for any point in time over the past year. No screenshots, no manual collection, no "trust me" conversations with auditors.
- Point-in-time validation for any date in the past 365 days
- Verifiable audit trails that map controls to assets to evidence
- Export-ready compliance reports in auditor-friendly formats
Graph-Powered Control Testing
Traditional tools test controls in isolation. JupiterOne tests controls in context. Our Security Asset Graph reveals what's actually connected to what, so you can validate controls based on the relationships that matter.
- Validate "no public S3 buckets contain PII" by tracing data classification to storage permissions
- Test "all production databases require encrypted connections" across your actual application topology
- Prove "privileged accounts use hardware MFA" by examining identity to access to authentication chains
Build Controls Your Security Program Actually Needs
Stop forcing your enterprise into generic framework templates. With J1QL, define the exact technical controls your organization implements. Instead of checking if MFA exists somewhere, write queries that validate:
- Which privileged accounts lack MFA across your actual privilege model
- What percentage of production access uses hardware tokens vs. software
- How many service accounts bypass MFA requirements and why