Unify and Secure Your Asset Data
JupiterOne consolidates asset data, identifies security gaps, and accelerates risk response for IT and security teams.
Asset Management
Exposure Management

Continuous Control Monitoring

Build your actual security controls. Monitor them continuously.
The only continuous controls monitoring solution built on a graph architecture, designed for security teams who've outgrown traditional compliance tools.
Real-time monitoring
Move from quarterly manual reviews to near-real-time monitoring

Built for Complexity
Purpose-built for mid-to-large enterprises managing multiple frameworks

Graph Powered Architecture
Define controls that reflect how your environment really works
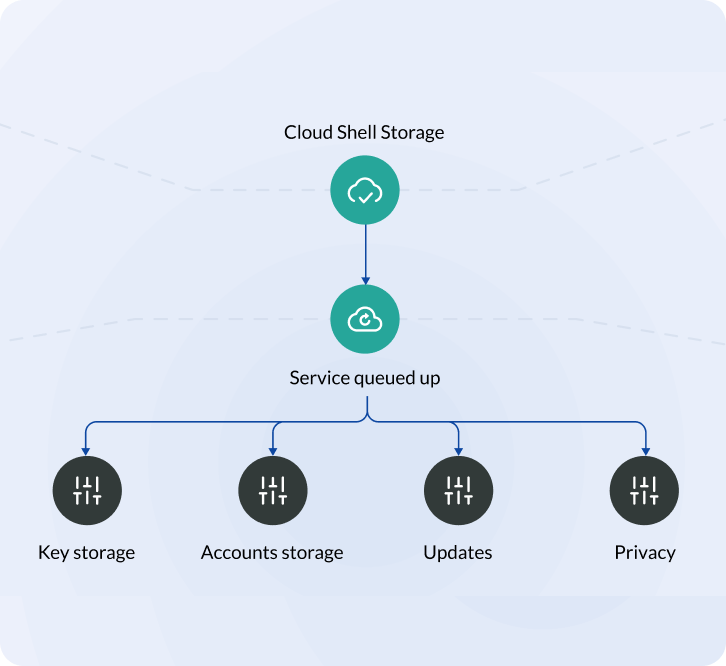
200+ Integrations
Get unified visibility into your entire cloud infrastructure

Security


Access Tools



Resources



Features
Why Choose JupiterOne?
Automated Discovery
Continuously identifies and updates asset data without manual effort.
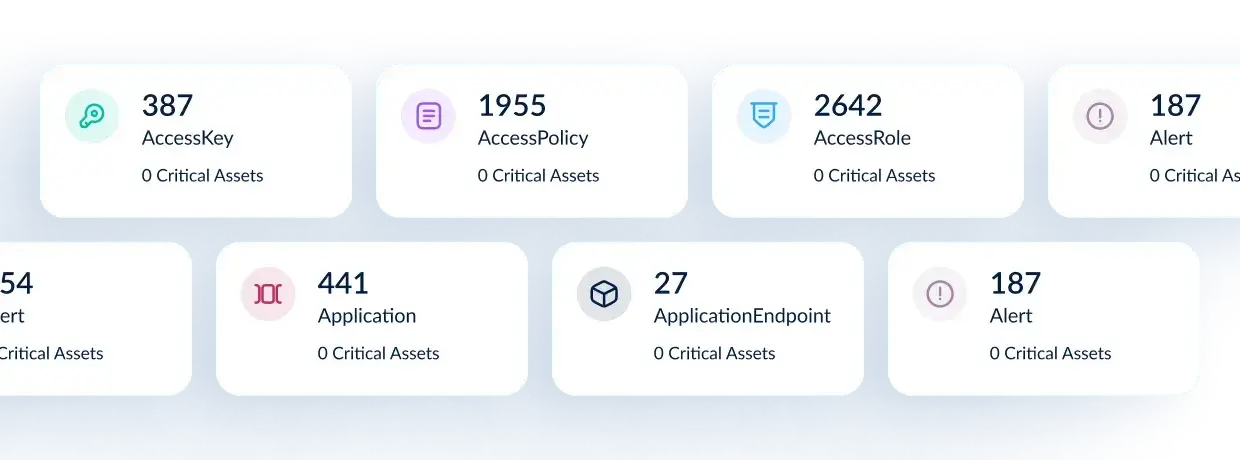
Security Insights
Maps asset relationships, highlights security gaps, and alerts teams to risks.

Unified Visibility
Consolidates assets from cloud, on premises, and hybrid environments in one platform.

Intuitive Interface
Navigate complex environments with clear visualizations and straightforward workflows.

See JupiterOne in Action
- Explore your environment in seconds.
- Identify misconfigurations and vulnerabilities instantly.
- Respond to risks with automated insights.



Solutions
Unified asset visibility, proactive risk management, and streamlined compliance for Security, IT and GRC teams



Cyber Asset Attack Surface Management
- Connect and normalize asset data from existing tools across cloud and on premises environments.
- Gain clear visibility into asset ownership, dependencies, and security posture.
- Eliminate blind spots to reduce your attack surface.



Continuous Threat Exposure Management
- Continuously identify misconfigurations, vulnerabilities, and security gaps.
- Prioritize risks based on real-time insights to reduce exposure.
- Improve collaboration between IT and security teams for faster remediation.



Continuous Controls Monitoring
- Map assets directly to security controls for improved compliance.
- Monitor and maintain control effectiveness to meet security frameworks.
- Ensure your security policies align with your evolving infrastructure.
How it works

1. Collect and normalize asset data
Connect with all your security and infrastructure tools. 200+ integrations bring visibility into your cloud and on-premises assets.

2. Map out assets and relationships
Automatically reveal unmonitored assets and map relationships to uncover gaps and risks.

3. Unified Visibility
Understand your entire attack surface to swiftly identify, prioritize, and remediate critical issues and vulnerabilities.
One platform for unified visibility into your entire attack surface
Cyber assets monitored
Discover more assets than any other platform. Including devices, code repos, users, and policies.
Reduced attack surface
Identify and eliminate outdated, ungoverned, and misconfigured assets.
Optimized operations
Reduce toil and manual tasks like identification of cyber assets or repeat investigations.
Award winning asset visibility & attack surface management software



Unify Your Asset Data
See every asset across your cloud, on premises, and hybrid environments in one platform.
Get a Demo































